In the vast universe of information security, web applications occupy an important place due to the wide range of data and functions they handle. However, this reliance on web applications also makes them an attractive target for cybercriminals and brings into discussion the importance of addressing vulnerabilities that could compromise their security. One such critical vulnerability is the insecure direct object reference vulnerability (IDOR). In this post we will discuss in depth what this vulnerability is about, how it can be found, some real cases, the importance of its impact for organizations and how to address this vulnerability from a security best practices perspective to prevent IDOR attacks.
Definition
IDOR vulnerability arises due to deficiencies in access control and identity validation in a web application. When an application fails to properly verify a user's authorization before allowing access to a specific object, an IDOR vulnerability occurs. This can occur when the application relies solely on client-supplied information, such as object identifiers in HTTP requests, without verifying whether the user has the proper permissions to access those objects.
It is necessary to know that this vulnerability in some cases is often the beginning of a more complex attack chain.
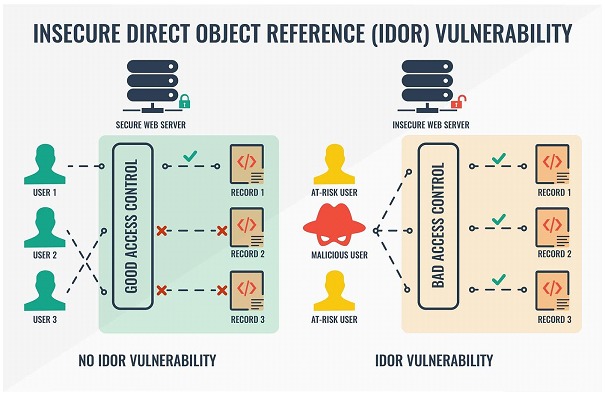
What is Broken Access Control?
This is a broader category of security vulnerabilities that includes the IDOR vulnerability, Broken Access Control is currently ranked as the most common vulnerability according to the OWASP study conducted in 2021. It refers to the inability of an application to impose appropriate restrictions on which users can access which resources. IDOR vulnerabilities are a subset of this broader problem and focus specifically on direct references to objects.
Understanding the object concept
To fully understand the IDOR vulnerability, it is important to be clear about the concept of "object" in the context of web applications. In object-oriented programming, an object is a single instance of a class that represents an entity with specific properties and behaviors. In the context of web applications, these objects can be any type of resource or data that the application handles, such as user profiles, files, database records, etc.
Examples
To better visualize how this vulnerability manifests itself in the real world, let's look at some examples:
Access to user profiles
Suppose a social networking application assigns each user a unique identifier and uses this ID in URLs to access user profiles (e.g. /profile/1234). If an authenticated user manually modifies the URL to access profiles that do not belong to him (e.g. trying to log in to user 1337 as “/profile/1337”), and the application does not validate this action, an IDOR vulnerability occurs.
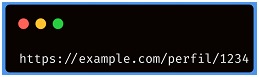
In this example, the authenticated user has access to his own profile by accessing "/perfil/1234". However, if the user modifies the ID in the URL to "/perfil/1337" and the application does not check for proper authorization, he could access another user's profile.
Direct reference to static files
IDOR vulnerabilities often arise when sensitive resources are located in static files on the server-side file system. For example, a website may save chat message transcripts to disk using a growing filename, and allow users to retrieve them by visiting a URL such as the following:
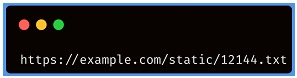
In this situation, an attacker can simply modify the file name to retrieve a transcript created by another user and potentially obtain user credentials and other confidential data. This also applies to web applications where files of other characteristics are stored, such as a file with a ".pdf" extension that may contain sensitive information about user data, banking transactions, medical test results, etc. Both examples are one of the many scenarios where this vulnerability is found.
Direct reference to database objects
Imagine a web site that uses the URL specified below to obtain information from a customer, extracting the data from the database.
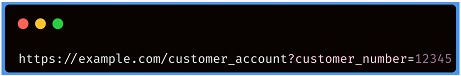
Here, the customer number is used directly as a record index in queries made to the database. If there are no other controls in place, an attacker can simply modify the "customer_number" value, bypassing the access controls to view the records of other customers. This is an example of an IDOR vulnerability leading to horizontal privilege escalation.
An attacker could perform horizontal and vertical privilege escalation by altering your user to one with additional privileges while bypassing access controls.
Potential impact
While we have already learned how this vulnerability could be exploited in a real case, it is just as important to be aware of the impact of an IDOR vulnerability can be significant and have serious repercussions for both individual users and the organizations that manage the affected applications, as this vulnerability can be the trigger for others making it potentially dangerous. Some of the most common impacts include:
• Leakage of confidential data: Attackers can access sensitive information, such as personal, financial or medical data, of other users.
• Data manipulation: Attackers can modify, delete or create unauthorized data, which can have catastrophic consequences for data integrity.
• Privacy violation: Users' privacy is compromised when their personal data is exposed to unauthorized persons, which can lead to a loss of trust on the part of users.
• Loss of reputation and trust: Organizations that are affected may lose the trust of their users due to the organization's inability to protect their data, which can result in a declining user base and long-term loss of revenue.
Prevention strategies
• Implement robust access controls: One of the most effective ways to mitigate the IDOR vulnerability is to implement robust access controls in the application. This involves verifying on each request whether the user has the necessary permissions to access the requested resource. Access controls can be based on roles, specific privileges or the principle of least privilege, where users only have access to the resources necessary to perform their functions. The ID (identifier) can also be replaced by the use of UUID (Universally Unique Identifier) in order to provide an extra layer of security in the web application.
• Use session and authorization tokens: Session and authorization tokens can help mitigate the IDOR vulnerability by providing an additional layer of security. Session tokens are used to authenticate users and verify their identity for each request, while authorization tokens are used to determine which specific resources a user is allowed to access. By implementing session and authorization tokens correctly, unauthorized access to application resources can be prevented.
• Validate user input: Proper validation of user input is critical to prevent IDOR attacks. This involves verifying all user-supplied data, such as object identifiers in HTTP requests, and ensuring that they are valid and authorized before processing them. However, it is also necessary to perform proper sanitization of all web application inputs. Input sanitization goes a step further by ensuring that the data is secure and does not contain any malicious code that can be used to manipulate the behavior of the application. By sanitizing inputs, special characters, SQL commands, HTML tags or other elements that could be used to perform data injection or manipulation attacks are removed. This significantly reduces the risk that cybercriminals can exploit the IDOR vulnerability by feeding manipulated or malicious data into the application.
• Implement Access Control Lists (ACLs): Access Control Lists (ACLs) are a useful tool for controlling and managing access to specific resources in a web application. By creating ACLs that explicitly define who has permission to access which resources, the risk of IDOR vulnerabilities can be significantly reduced. ACLs can be based on user roles, user groups or specific authorization criteria to ensure that only authorized users can access relevant resources.
• Perform regular security testing: Regular security testing, such as penetration testing and security audits, is critical to identifying and remediating IDOR vulnerabilities in a web application. These tests can help identify potential weaknesses in access control and input validation, as well as assess the effectiveness of implemented mitigation measures. By performing security tests on a regular basis, you can ensure that your application is protected against the latest security threats and vulnerabilities.
• Keeping up to date with security best practices: As security threats are constantly evolving, it is important to keep up to date with security best practices and the latest mitigation techniques. This may include participating in computer security training courses, following recommendations from organizations such as the Open Web Application Security Project (OWASP), and staying on top of security updates and patches for frameworks and libraries used in the application.
By implementing these mitigation measures and remediating the IDOR vulnerability, organizations can significantly reduce the risk of exposure to attacks and protect the integrity and confidentiality of their users' data. However, it is important to remember that web application security is an ongoing process and must be addressed proactively and systematically to ensure effective protection against security threats.
Conclusion
IDOR vulnerability is not only a technical issue, but also an ethical and legal responsibility for organizations that manage web applications. Protecting the integrity and confidentiality of user data is critical to maintaining customer trust and complying with privacy and data protection regulations.
Ultimately, mention that this vulnerability is a serious threat that requires attention and action by developers, information security teams and organizations as a whole. By taking proactive steps to identify, remediate and prevent IDOR, we can strengthen the security of our web applications and in turn protect sensitive user data in the ever-changing IT security threat landscape.