The challenges related to Digital Identity security have evolved over the last 20 years, but have accelerated dramatically since the global Covid19 pandemic with the massive migration of employees to work remotely and mostly without the need or intention to return to the office beyond one or two days per week.
Securely managing Digital Identity based on traditional models of securing the perimeter has become obsolete when most of the activity happens outside the corporate network.
In this article we will review some basic concepts related to Digital Identity, the pillars on which the management and protection of Identity is based, statistics and some good practices to implement to improve the protection of Digital Identity.
Definition
We can examine the definition of Digital Identity provided by the National Institute of Standards and Technology (NIST), which defines it as "a set of attributes or characteristics that describe an entity in cyberspace".
Further elaborating on this definition, it can be said that Digital Identity is a set of attributes that uniquely represent a person, entity or device in the Digital environment. These attributes can include usernames, passwords, email addresses, identification numbers, and other unique identifiers, as well as biometric data such as fingerprints or facial recognition.
In essence, Digital Identity is the way in which a person or entity is recognized and authenticated in cyberspace, allowing them to access services, applications, perform transactions and communicate on-line through different media. This Identity can be used in a variety of contexts such as accessing social network accounts, business applications, critical assets of organizations, online banking operations, etc.
Typology
Although there are many types of Digital Identity, they can be primarily grouped as follows:
• Human Digital Identities: Allow human users to have access to assets within a network. Human Identities can be divided into employees, contractors, vendors, customers, among the main types
• Non-human Identities: These are mechanisms that allow non-human entities to be authenticated within the infrastructure or applications. Among these Identities, we can mention service accounts, sensors, RPAs, servers, desktops, laptops, etc.
• Cloud Identities: These types of Identities are used to access resources in the cloud. They are highly dynamic and often have some kind of important privilege.
Some indicators
It is easier for a cybercriminal to try to steal credentials than to hack into an asset.
Identity has become the predominant means by which cybercriminals attempt to penetrate organizations.
A survey conducted this year by the Identity Defined Security Alliance of a broad universe of companies with more than 1,000 employees showed the following indicators:
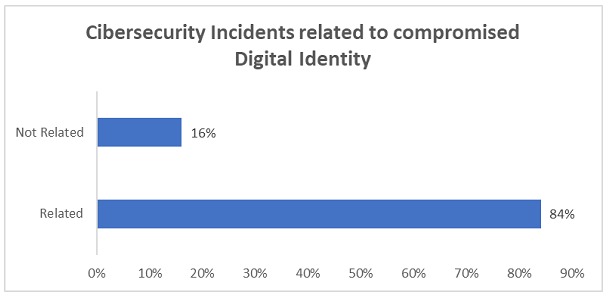
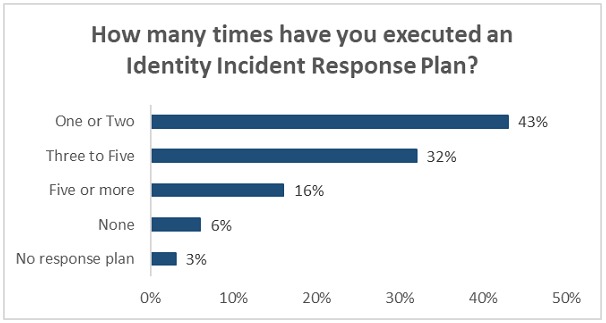
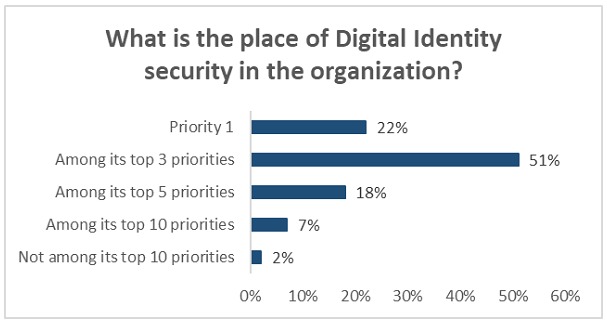
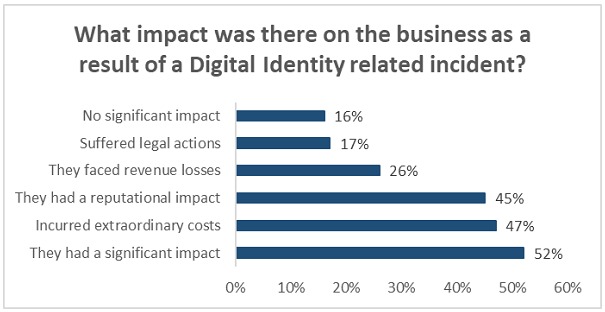
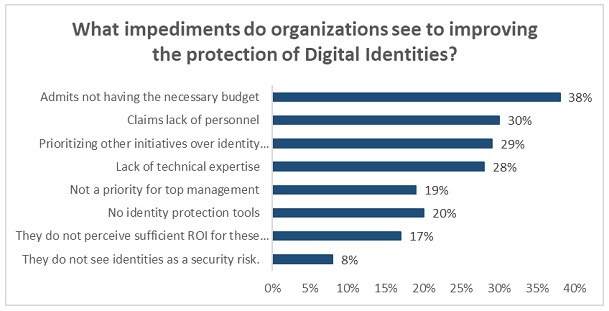
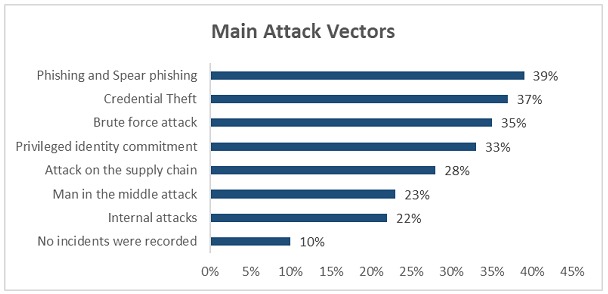
Pillars of Identity Protection
The perimeter is increasingly frequently Identity-based so cyber attackers continue to invest in technologies, innovations and processes to penetrate organizations through an Identity-related security breach.
In contrast, companies dedicated to the development of solutions that help secure Digital Identity continue to invest in innovation and development of new features to their products that increase protection in this area.
There are currently three critical components to the management of access and governance of Digital Identities:
• Access Management
• Privileged Access Management
• Identity Governance Management
The automation, interoperability and integration of these three components are essential to ensure that the infrastructure, applications, policies, processes and procedures work together to ensure a high degree of protection of Digital Identities in all areas of the organization.
Access Management (AM)
Access management strengthens identity security and reduces risk by ensuring that users have authorized access to resources specific to their role.
Most access management solutions provide access privileges through Identification, Authentication and Authorization to applications and infrastructure.
Privileged Access Management (PAM)
Privileged access management is a critical security control that allows organizations to optimize management and monitoring across infrastructure, applications, databases, firewalls, networks, etc.
Managing privileged access is a challenge for many organizations because holders of highly privileged accounts have access to both infrastructure and sensitive organizational data. The three main types of privileged accounts are:
• Administrator Accounts: They are used to modify configuration files and operating systems.
• System accounts: These are accounts with unrestricted access to services or data on the organization's servers and become the main target of cybercriminals.
• Service Accounts: They can usually access data, resources and configurations to run processes and applications automatically and unattended.
Identity Management and Governance
Identity management and governance manages the lifecycle of Identities in the organization, automating and certifying user accounts, providing provisioning to applications based on a matrix of roles and functions, defining management policies and offering broad visibility of Identities and their access privileges. By streamlining these processes, organizations can have better control of who accesses which application, when and why.
Digital Identity Protection Challenges
The proliferation of digital services has significantly increased the number of Identities that an organization must manage, on the other hand, the growing sophistication of cyber threats that can lead to incidents such as identity theft or impersonation, financial fraud or unauthorized access to sensitive information or critical infrastructure of organizations.
In addition to the challenge that Digital Identity protection represents for organizations, there are other points of interest to take into account when planning the implementation of one or more initiatives aimed at improving Digital Identity security:
• Obtaining internal consensus: Internal consensus on the prioritization, funding and allocation of resources among the different areas of Business, Technology, Operations, CISOs, Human Resources, Audit, among others, regarding the initiatives to be implemented is a task of vital importance to avoid detractors and obstructors of the tools to be implemented.
• Regulatory Requirements: A wide range of industries must comply with different regulatory and/or compliance standards imposed by the authorities, so a thorough analysis is necessary when selecting the tools that best help regulatory compliance.
• Internal and External Audits: In general all companies are subject to different types of internal audits and some must comply with external audits. It is essential that Digital Identity management tools provide the necessary elements and data to comply with each type of audit.
• New threats: Every day new threats emerge that aim to violate the Digital Identity, seeking to gain access to the assets of organizations. It is necessary to know the development roadmap of the different platforms to be alert and implement features that help prevent new threats.
• Cost-benefit analysis: Each initiative must have an exhaustive cost-benefit analysis and different alternatives to ensure buy-in from key stakeholders.
Best Practices
For the correct implementation and operation, it is recommended to consider the following best practices, both from a strategic and operational point of view.
Conduct a comprehensive assessment of the state of protection in the organization.
The first step is to assess the current state of the Digital Identity security level of all human and non-human Identities to correlate Identity data with all the organization's resources, infrastructure and applications.
The Identities and accounts involved will include a combination of human and non-human Identities.
A disaggregated view of Identity data is necessary to understand what Identities exist and how they are being used. This helps you assess baseline risk and measure security improvement as you implement policies and improve controls.
Establish an Identity governance committee.
Integrating an identity governance committee is essential for the management and protection of digital identities within an organization.
Its objective is to establish policies, standards and guidelines to ensure effective and secure management and governance of Identities and access.
It should be made up of different areas of the organization, including Technology, Information Security, Human Resources, Finance and Legal. Depending on the organization, other areas may need to be involved in this committee.
Implement a comprehensive Identity and access security policy.
This policy should govern how access to the organization's applications and assets, including privileged access, is managed. This policy should also define and implement information governance (also called data governance). This involves appropriate data privacy and security practices, such as data collection, handling, transmission and disposal.
Ensuring the uniqueness of both human and non-human Identities
Uniqueness of Identities is the DNA of your IAM Digital Identity assurance program A unique entity catalog is important and mandatory. If you cannot guarantee that each Identity is unique and associated with an owner, you are potentially in the presence of a critical breach.
Define and implement a Role-Based Access Matrix (RBAC)
Creating a role-based Access matrix enables each Identity to be assigned a unique role associated with its function within the organization. This allows for independence and control that users associated with the identities have access only to the applications and/or infrastructure necessary to perform their functions, reducing the risk of unauthorized access.
Apply Multi-Factor Authentication (MFA)
Multifactor authentication (MFA) has proven to be a very effective technique to prevent credential theft either by carelessness or by social engineering techniques such as phishing, vishing, smishing, etc.
It allows adding an additional layer of control and although it may suffer some kind of attack such as MFA bombing or MFA fatigue. This technique is still highly effective in preventing identity theft, improving the security posture of the organization.
Apply Single Sign On (SSO) technologies.
Implementing SSO offers an efficient way to manage identities and accesses in an organization as users currently need to access multiple applications to perform their daily tasks and tend to use weak or very similar credentials for all accesses and store them in places that expose them to risk of loss or theft.
On the other hand, an SSO solution allows to establish secure credential policies in a consistent way, improve the user experience, simplify the management of Identities, save time and costs due to the need of administrative steps when a credential is forgotten or lost.
User Training and Awareness
Within organizations, employees are one of the main attack vectors when it comes to breaching the security of an organization.
While there are tools, technologies, policies and controls to help protect Identity security, it is critical to train all of your employees on the types of Identity-based threats they are likely to encounter.
An annual awareness and training program should be implemented so that employees are trained to identify suspicious emails, social engineering attacks and other activities and report them to the areas in charge of information security, as well as to other areas that are responsible for informing the rest of the company about the attacks received.
Conclusion
Today, digital identity has become a central and fundamental component in the security and operational structure of organizations. It encompasses not only the management of an individual's credentials and attributes to access applications, but also their interaction with various services and platforms throughout their digital life.
This reality has transformed the way in which access to critical resources and data is managed, protected and monitored.
Digital identity security incident statistics reflect a growing concern about the vulnerability of authentication and identity management systems and how to mitigate them.
Meeting these challenges requires a thorough understanding of the threats and an effective implementation of security strategies, which should not be entirely technological but also a continuous education and training of technical teams and an ongoing user awareness program to identify and respond to potential threats.