OT asset management is crucial to ensure the availability and integrity of industrial processes, safeguard data confidentiality, and improve business profitability.
The first link in an asset management system is the inventory, which represents a list of all the resources (physical, software, documents, services, personnel, facilities, etc.) valuable to the organization that require protection against possible risks and threats.
Maintaining an updated inventory in industrial environments, or creating one from scratch, represents a great challenge, the changes caused by the Industry 4.0 paradigm and the evolution of the Internet of Things in industry (IIoT) have modified the ways of organizing the means of production, as a large number of devices are usually deployed to achieve greater control and along with them a greater number of sensors, actuators and gateways for the concentration of communications, generating an amount of data traffic almost unmanageable by some traditional infrastructures.
It is common to find an incomplete or non-existent inventory of assets in this type of environment, which is one of the major drawbacks when addressing other improvements in the cybersecurity of these systems, since you cannot protect what you do not know, so it is important to have an inventory of assets conveniently updated and reviewed.
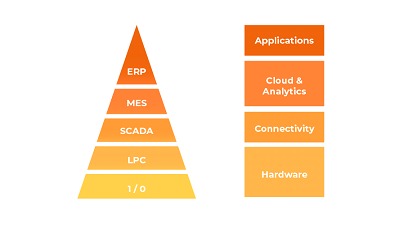
No longer can one rely solely on traditional IT-based approaches or physical control systems, threats are constantly evolving, and attacks on critical infrastructure and industrial control systems are becoming more sophisticated and common.
Investing in this type of implementation brings important operational benefits, such as: reduction of downtime by anticipating problems, greater operational efficiency that reduces costs and optimizes resources, decision making based on data generated by the assets, and regulatory and industry compliance del sector (NIST, ISA/IEC 62443, ENS, COBIT, SOX), which not only helps the business, but also aligns us with market demands.
Effective OT asset management is based on two key complementary elements: OT asset usage policy and a comprehensive inventory as mentioned above.
The mission of the Asset Use Policy is to regulate the responsible and secure use, management and protection of OT devices and information assets and has a direct impact on the inventory.
Among the procedures included in this policy are:
• Regulations for the acquisition of fixed assets in the company.
• Procedure for recording fixed assets.
• Rules for the proper use of assets.
• Procedure for the creation and maintenance of inventories.
• Steps for assigning asset managers.
• Steps to insure the company's fixed assets.
Benefits of an updated asset inventory
Improvement against possible cyber-attacks: If we know our environment, we already know what we have in the network. We can deploy solutions that allow us to filter by CPE (Common Platform Enumerations) and associate models, systems, technologies, etc. with specific vulnerabilities.
Improved network architecture security: Enables efficient development of other projects such as network restructuring, probe deployment, etc.
A network without proper segmentation within an industrial organization allows, in the vast majority of situations, attackers to take control of both the IT and OT sides.
Therefore, it is important to implement other projects that help to improve cybersecurity in industrial environments, always taking the asset inventory as a reference.
Other implications: Device fault identification. Sometimes, the simple fact of having controlled devices and communication flows can help in other areas that improve the efficiency of industrial processes. On the other hand, the inventory is essential to feed the SIEM platform that manages the events associated with each asset.
Scope of the environment analysis
This does not refer to the number of assets to be included when analyzing an industrial environment, but to the level of detail that the information collected on each asset will have and how it is presented (excel table, json, any specific requirement of the technology that will consume it, etc.). In the case of being the first one, it is recommended to include a basic information collection that allows to control such assets. Next we will see some examples of how to classify them.
Clasificación de activos en el inventario
The inventory should have a global approach covering all systems within its scope and should include PLC, DCS, SCADA, as well as supervisory elements such as HMI and other auxiliary devices and systems. To facilitate the management and maintenance of the inventory, it is convenient to classify the assets by categories, according to their nature:
• Datas: All data (in any format) that is generated, collected, managed, transmitted and destroyed. Databases, documentation (user manuals, contracts, regulations, etc.).
• Applications: Software used for process management. SCADA systems, HMI development tools, applications developed, operating systems, device firmware, etc.
• industrial hardware: Physical equipment required to perform industrial work (remote terminals, PLCs, IEDs, PCs, servers, mobile or handheld devices, etc.).
• Network: Network connectivity devices (routers, switches, hubs, gateways, etc.)
• Technology: Other equipment necessary to manage the company's people and business (servers, user equipment, telephones, printers, routers, cabling, etc.).
• Personnel: This category includes the organization's own staff as well as subcontracted personnel, maintenance personnel and, in general, all those who have access to the industry in one way or another.
• Facilities: Places where the relevant systems of the system are housed (offices, buildings, electrical installations, vehicles, etc.).
• Auxiliary equipment: This type includes all those assets that support the information systems and are not included in any of the previously defined types (data destruction equipment, air conditioning equipment, UPS, etc.).
• Documentation: Any asset containing information on industrial processes or other sensitive information.
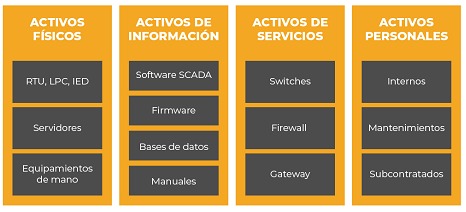
Identification of each asset
To be of value in safety assessment and risk management, an asset inventory must provide sufficient information for future projects or incidents, as well as provide an accurate picture of the asset values so that it is possible to establish the criteria for performing a risk analysis.
To do this you must collect relevant information from each system such as:
Name: May include model, brand, descriptive name, etc.
Description: It does not need to be very long, but it should contain information on the use of the asset.
Physical Identifier: Unique code for the physical asset (Label, QR, Barcode) that allows a quick relationship in the logical table. It must follow a pattern chosen by the company
Type: This includes the group to which the asset belongs and its category, as we saw in the previous comparative table, to all those related to hardware we could add, as appropriate, the following items:
• Productive Line
• MAC Address
• IP
• Manufacturer
• Serial Number
• Model
• Firmware version
Owner: Every asset must have an owner. This owner will be in charge of making decisions such as the replacement of the asset.
Manager: The manager is the person in charge of ensuring that the asset is operational, as well as managing access to it. In many occasions it may coincide with the owner.
Location: Place where the asset is physically located. If it is a physical asset the location will be a place, if it is a logical asset the location will be a physical asset.
Asset valuation: Value to be assigned to the asset to assess its impact on the system. For this purpose, several parameters can be taken into account, such as:
• Availability: Qualitative or quantitative value that determines the importance of the absence of the asset.
• Integrity: Qualitative or quantitative value that determines the repercussions for the business that would result from unauthorized modification of the asset.
• Confidentiality: Qualitative or quantitative value that determines the degree of confidentiality required by the asset.
• Criticality: Value that determines the dependence of the process on the asset. The higher the criticality value, the greater the consequences for the business if the asset is lost.
• Cost: Economic value of the asset.
Each field is relevant and of great importance to the asset inventory, some organizations also incorporate information on the Purdue level at which the asset is classified. This allows to better define the possible tasks that the asset performs within the industrial process and serves as a ranking method to see the importance of the asset. To execute a scope extension of an existing inventory, it is recommended to include fields that provide extra cybersecurity value such as:
Services and open ports: Controlling the ports that the industrial device has available through the network and the services that are running on them, allows for greater control of industrial communications.
Assets with which it communicates: Knowing the assets with which another asset has to communicate not only allows to control the communication flows as in the previous case, but also facilitates the creation of communication baselines for the detection of anomalies in the network.
Deployed software: Having knowledge about the software and versions running on an asset allows to control future vulnerabilities detected in them.
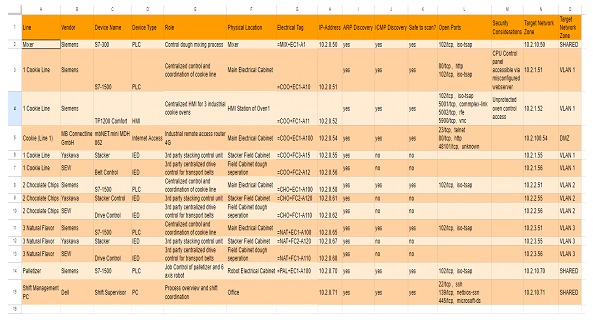
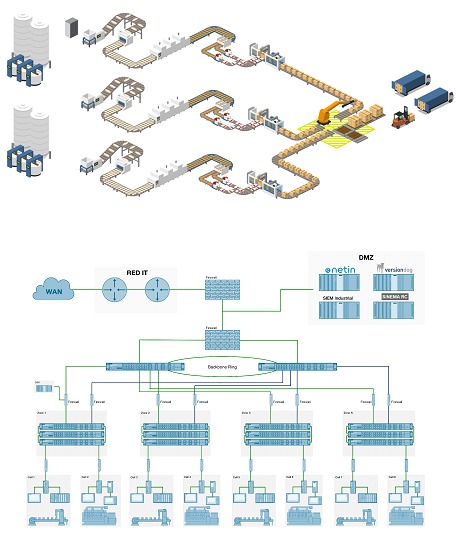
The number of fields can vary or become more complex depending on the maturity stage of the organization. Additionally, as additional documentation, network topology and production process diagrams can be generated, here are some examples:
Forms of implementation
Once the scope has been defined, it is necessary to be clear about the form that will be chosen to carry out the arduous task of implementing an asset inventory. In this sense, there are 3 options to carry out an asset inventory:
Manual
The information for each asset is collected by one or more persons, who fill in the fields previously defined in the scope, without the help of any complementary software. It is advisable to use this option when the industrial organization is not too large or the assets are not spread over a large area. It is also advisable to use this option when the organization has assets that are not connected to a network or when serial communications are used.
Automatic
This way of implementing an asset inventory is based on the use of tools that allow to collect the information defined in the scope about each asset in an automatic way. This way of implementing an asset inventory is recommended when the industrial organization has a large number of devices, or they are located in different locations. An example of this type of tool is OT BASE. This tool allows asset discovery using communication protocols for device discovery such as SNMP, LLDP, Ethernet/IP, queries through WMI, etc.
Mixed
It is the most complete way to implement an asset inventory and the most recommended, regardless of the organization where the information is collected. It is based on the use of both automated tools and manual techniques to achieve greater accuracy when collecting information.
Methodologies and Technologies
Based on the way you choose to implement the asset inventory, you can opt for a series of methodologies that, among other factors, depending on the environment in which we will run the tests, can be adjusted more or less to the required needs. Some of the methodologies that can be followed when implementing an asset inventory are:
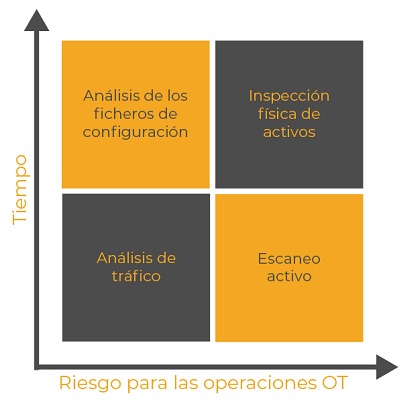
• Physical inspection of assets: Complex to execute in large facilities spread over different locations. Can also be dangerous in certain areas.
• Traffic analysis: Reduced analysis time and non-intrusive approach.
• Active scanning: Fast methodology in its execution, but with possible impacts on OT operations.
• Configuration file analysis:Good option when devices are known. Time consuming and does not have a major impact on operations in industrial environments.
Claroty
This solution offers several types of probes, each designed to address different needs and environments:
Gateway Probes:
Associated product: Claroty Continuous Threat Detection (CTD).
Claroty's gateway probes integrate with the CTD product to provide real-time visibility and threat detection in industrial environments. They monitor network traffic at network gateways to identify malicious activity and anomalous behavior.
Ingress Probes:
Associated product: Claroty Secure Remote Access (SRA).
Entry probes are used with the SRA product to ensure security at industrial network entry points, such as remote access connections and Internet connection points. They help protect these critical points against potential threats and cyber attacks.
Plant Probes:
Associated product: Claroty Asset Discovery and Monitoring (ADM).
Plant probes are deployed with the ADM product to provide visibility and monitoring of industrial devices within the plant. They detect and monitor device activity to identify potential threats and ensure the integrity of the industrial network.
Cloud Probes:
Associated product: Claroty Secure Access Service Edge (SASE).
Cloud probes integrate with the SASE product to extend security to cloud environments used by industrial organizations. They monitor traffic between local infrastructure and cloud services to identify potential threats and vulnerabilities in these environments.
These partnerships between probes and Claroty products show how each type of probe is complemented by a specific product to provide a complete industrial cyber security solution in different areas of an organization's network and IT environment.
Other Tools
For all those production lines that are out of reach of the probes, some of the following tools will be used to carry out the inventory:
Security Onion distribution adapted to industrial environments: This distribution allows, among other tasks, network monitoring. Thanks to the implementation of the various tools present in this Linux distribution, it is possible to develop an asset inventory.
GRASSMARLIN: Fully passive tool that allows the visualization of assets through a network map.
NMAP (Claroty Edge): A tool that allows to perform active scans through the network to obtain information about the assets present in the industrial network. Among the information that can be obtained are the active ports, services running and versions of the solutions behind those services.
Conclusion
One of the great advantages of having an asset inventory is that asset management becomes much easier. If the asset inventory has been implemented correctly, the industrial organization can enjoy the following advantages:
• Discovery: The organization will be able to establish a complete baseline at both the physical and logical level of each asset in order to detect potential problems.
• Identification: For each asset you will have stored different attributes such as model, operating system used, protocols used, MAC address, patch level information, firmware versions, etc.
• Visibility: The industrial organization will have sufficient capacity to detect the connection and disconnection of devices to the network, the IP associated with each one and the serial connections that industrial devices may have.
• Disposition: To know the level of criticality, commonly qualified as high, medium and low of each particular asset. In addition, the industrial organization will be able to know the relationship between assets through the TO network and the communications they may have (including the series).
• Alert Capabilities: Having a deep knowledge of each asset allows the industrial organization to detect deviations in the processes involving some assets.