Vulnerability CVE-2024-37085 is an authentication bypass flaw in VMware ESXi hypervisors, specifically in their integration with Active Directory (AD). This vulnerability allows an attacker who already has limited access to a server to escalate their privileges and gain full administrative control over the ESXi hypervisor. This is especially critical as hypervisors manage multiple virtual machines (VMs) that are essential for network operations.
This vulnerability was discovered and published on June 25, 2024 and, since its publication, VMware has released updates to address the issue. The updates include patches that fix the authentication bypass and ensure that the hypervisor correctly validates the existence of groups before granting administrative permissions. However, it is important to note that VMware has no plans to provide patches for older versions, such as ESXi 7.0 and VMware Cloud Foundation 4.x, leaving organizations using these versions in a vulnerable position if they do not migrate to newer versions.
How it works
The problem lies in the fact that ESXi hypervisors, when joining an Active Directory domain, do not verify the existence of a group called "ESX Admins". This group is not a built-in feature of AD and does not exist by default. However, once the hypervisor is joined to the domain, any member of a group named "ESX Admins" is automatically given full administrative permissions, even if that group was created by an attacker. This means that an attacker can create this group and add a user controlled by him, giving him full access to the hypervisor.
Exploitation Methods
Microsoft has identified three main methods to proceed with the exploitation:
• Creating the "ESX Admins" GroupAn attacker can create this group in Active Directory and add a user, which grants administrative access to the ESXi hypervisor. This is the most direct and commonly used method.
• Rename Existing Groups: Attackers can rename any existing group in the domain to "ESX Admins" and add users or use existing members to gain administrative privileges. This allows attackers to bypass security controls that might be in place.
• Persistent Administrative Access: Assigning administrative privileges to other groups does not remove members of the "ESX Admins" group. This means that attackers can maintain unauthorized access even if changes are made to permission settings.
Its use in Ransomware attacks
Since this vulnerability was identified, several ransomware groups, such as Storm-0506, Akira and Black Basta, have begun to exploit it in post-compromise attacks. These groups use the vulnerability to encrypt the hypervisor file system, allowing them to carry out ransomware attacks that can be devastating to affected organizations. The ability to encrypt critical data in a virtualized environment can lead to significant financial losses and disruption of business operations.
Attack dynamics
Microsoft has observed that the Storm-0506 group exploited this vulnerability to deploy Black Basta ransomware at a North American engineering firm. They first gained initial access through a Qakbot infection, then escalated privileges by exploiting CVE-2023-28252 in Windows and stole domain administrator credentials with Pypykatz. Finally, they created the "ESX Admins" group to gain full control of the ESXi hypervisor and encrypt virtual machines.
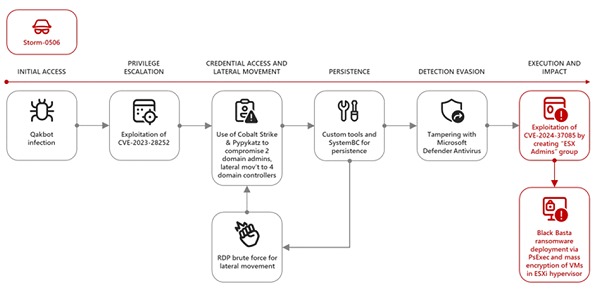
• Initial Access: Attackers generally gain initial access to an organization's network through phishing techniques, malware or vulnerabilities in other systems. Once inside, they seek to escalate privileges.
• Privilege escalation: Using other vulnerabilities, such as those affecting Active Directory, attackers can elevate their privileges. For example, they can exploit vulnerabilities in the operating system to obtain domain administrator credentials.
• Vulnerability Exploit: With administrative access to Active Directory, attackers can create or rename a group to "ESX Admins" and add a user controlled by them. This gives them full access to the ESXi hypervisor, as the system does not validate the existence of the group, allowing any group with that name to grant administrative permissions.
• Data Encryption: Once attackers have access to the hypervisor, they can encrypt the ESXi hypervisor file system and thus the virtual machines running on it. This can result in loss of access to critical data and disruption of business operations.
• Ransom Demand: After encrypting data, attackers often demand a ransom from the organization to unlock access to the information. This may include threats of leaking sensitive data if their demands are not met.
Mitigation and Recommendations
To protect against exploitation of CVE-2024-37085, organizations should:
• Apply Security Patches: VMware has released updates for VMware Cloud Foundation 8.0 and 5.x versions. However, there are no patches planned for versions 7.0 and 4.x. It is crucial that organizations upgrade to the supported versions.
• Verify the Existence of the "ESX Admins" Group: Ensure that the group is correctly configured and hardened within the domain. This includes disabling automatic administrative access for this group.
• Adjust Security Settings: Modify the advanced settings of the ESXi hypervisor to deny access to the "ESX Admins" group. This can be done by changing the advanced Config.HostAgent.plugins.hostsvc.esxAdminsGroupAutoAdd option to false.
• Monitor Active Directory Activities: Perform regular audits of Active Directory groups, especially those with elevated privileges, to detect potential intrusions.
• Implement Detection and Response: Use intrusion detection systems (IDS) and monitor ESXi logs to identify suspicious behavior that may indicate an attack.
Conclusion
In summary, CVE-2024-37085 is a critical vulnerability that requires immediate attention. By applying patches, implementing robust security controls and maintaining a strong security posture, organizations can significantly reduce the risk of falling victim to attacks that exploit this flaw in VMware ESXi.